Kubernetes on Azure
Context
The purpose of this document is to describe how to create the necessary infrastructure to deploy Vectice on a Kubernetes cluster in Azure, followed by instructions to deploy the Vectice software
Understanding prerequisites
Infrastructure requirements
#
Requirement
Notes or Details
1
Security Groups
Port 443 (HTTPS)
3128 Outbound (pip install)
SMTP Port (e.g 2525)
2
Kubernetes Cluster
v1.16+ deployed
2 nodes with Standard_B4ms
3
Azure Blob Storage Container
In the same region
4
Azure Database for PostgreSQL flexible server
13.x Cloud SQL instance
Other requirements
#
Requirement
Notes or Details
5
Domain Name
Example: https://vectice.my-company.com
6
SSL Certificate
Must be associated with the domain name above
Self-signed certificates are not recommended
Deployment environment with the following tools:
2. How to provision the infrastructure
You have two ways to create the infrastructure necessary for running Vectice.
Provisioning via Terraform (with Terragrunt Wrapper)
Expected Time: 40 minutes
Steps:
Complete instructions, including the Terraform script, are found in the package your Vectice account team provided you. Contact [email protected] if you require assistance.
Provisioning via Azure portal
Expected Time: 2 hours
Steps:
PostgreSQL Instance creation, see Appendix 1: Creating the SQL Instance
Kubernetes cluster creation, see Appendix 2: Cluster Creation
Blob Storage Creation, see Appendix 3: Creating the Blob Storage container
3. How to deploy the Vectice application
The provisioning of Vectice on Kubernetes will happen in 5 steps:
Step 1: Connect to the Cluster and Create the Vectice Namespace
Step 2: Install the Cert Manager
Step 3: Set up the Application Gateway on the cluster
Step 4: Create Secrets for Ingress and Docker Image Retriever
Step 5: Install the Vectice Stack
For any questions or assistance with deployment, please reach out to [email protected]
Step 1: Connect to the cluster and create the Vectice namespace
First, define the variables for the next steps and retrieve connections from your deployment machine. Below, sample values are provided between brackets:
The expected output should look like this:
Next, test the connection:
The expected output should look like this:
Finally, create the Vectice namespace where applications will be deployed:
Step 2: Install the Cert Manager
Next, install the cert-manager and cert-manager-csi-driver applications on the cluster.
Cert-manager is used to implement SSL for internal communication between Vectice pods, Cert-manager-csi-driver will attach a csi volume containing the certificates to the Vectice pods
Next, generate a custom Certificate Authority and create its associated secret:
Step 3: Set up the Application Gateway on the cluster
To enable the AGIC add-on, go to the Kubernetes services page and select your Cluster. Go to the Settings > Networking and Virtual Network Integration tab to find the application gateway ingress controller section. Click on the ManageCheck box next to Enable ingress controller, and Create a new Application Gateway or Select your existing one.
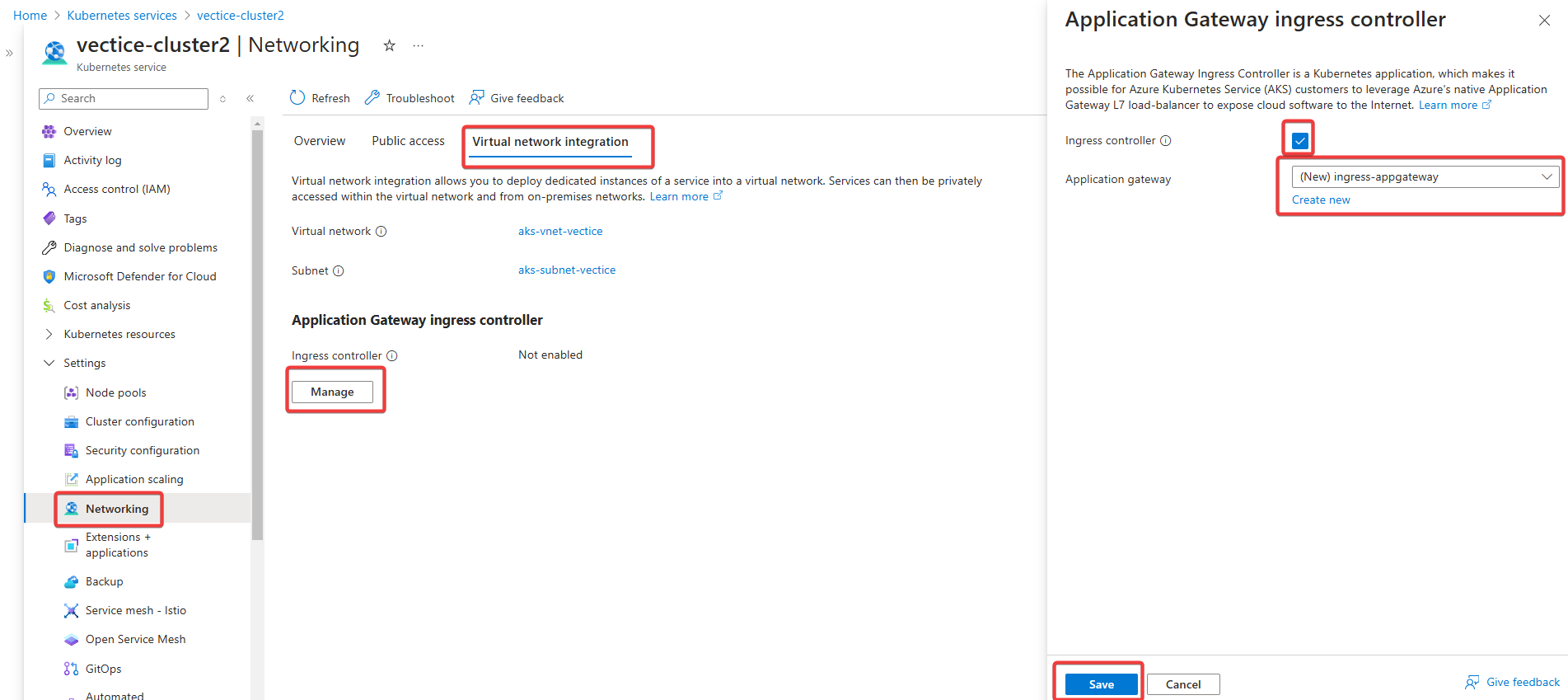
If you did not have an existing Application Gateway, the creation could be blocked because of a permission issue. The AG needs to create a subnet on the Vnet used by the AKS Cluster.
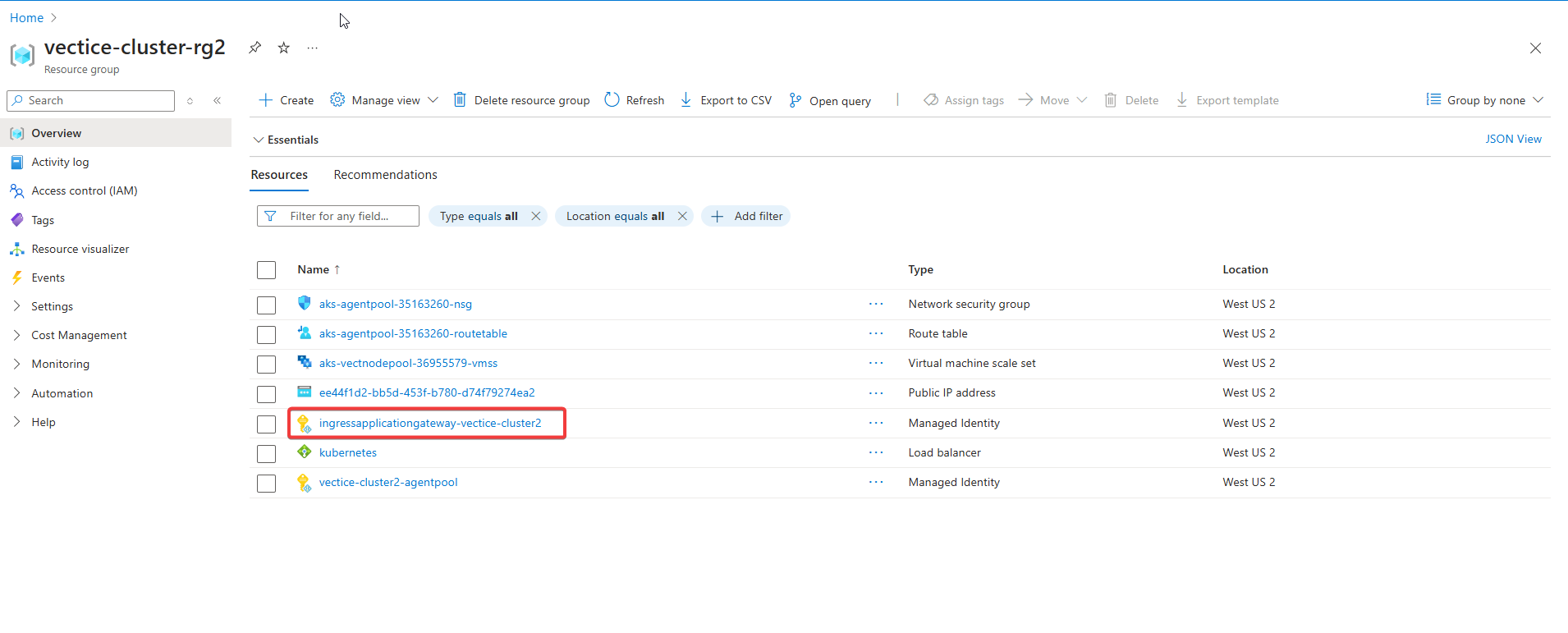
As the AG belongs to the Managed Resource Group of the AKS cluster, permission is needed to add on the Managed Identity of the AG.
Navigate to the AKS managed Resource group created along with the cluster and Click on the managed Identity that contains the name of your AG (it might take a few minutes to appear).
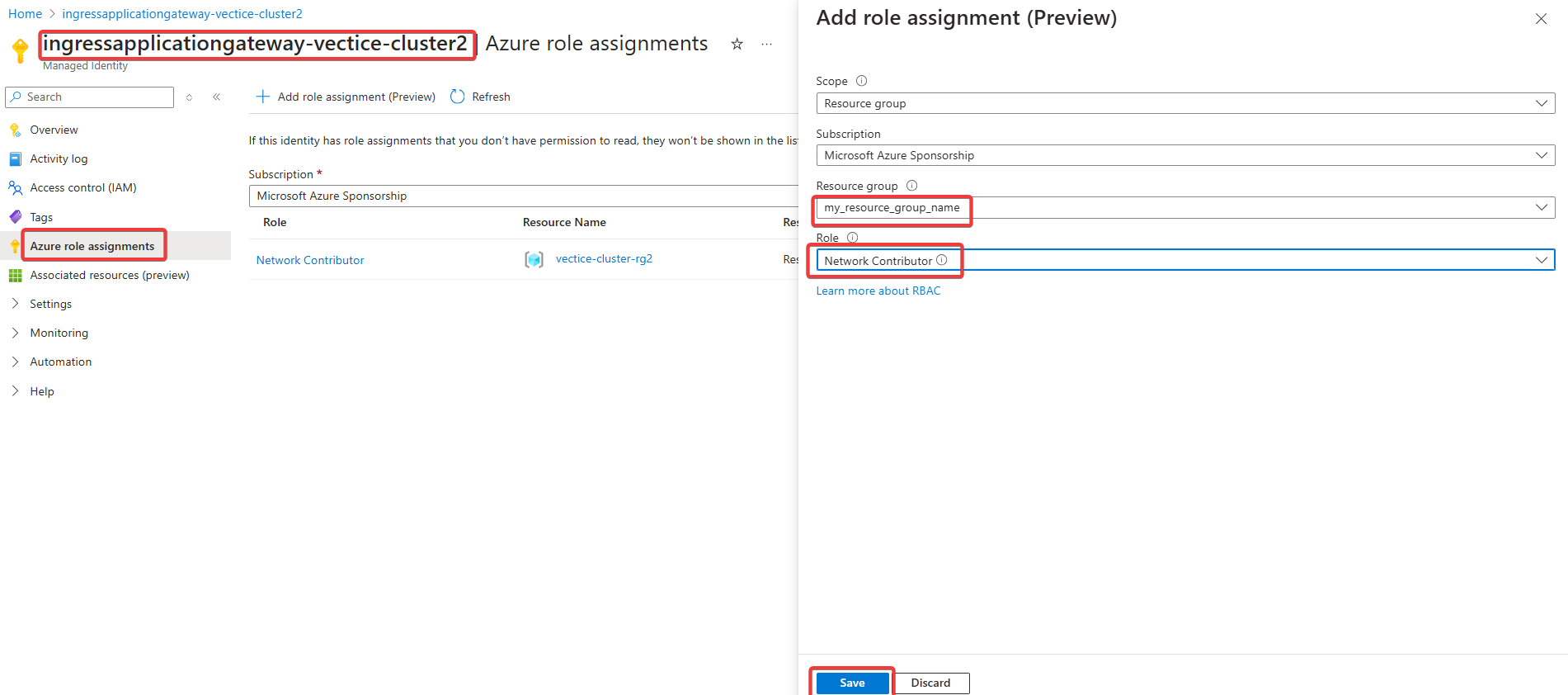
Navigate to the Azure role assignment menu, and add the role "Network Contributor" to the general resource group you use for the resources (not the AKS managed resource group).
Add root-certificate to the application gateway
Once the application gateway is created, add the root certificate to the application gateway. Below, sample values are provided between brackets.
Step 4: Create Secrets for Ingress and Docker Image Retriever
First, create a self-signed certificate using the following command, replacing the item highlighted with your own Common Name (CN). Below, sample values are provided between brackets.
Then, use the command below to install your certificates in the cluster
To deploy the software, you can retrieve the necessary Docker images directly from the Vectice Registry. Alternatively, if you prefer, we can provide the images via an alternative delivery method that would be defined together. If your Kubernetes cluster is configured to pull images directly from the Vectice Registry, navigate to the location of the “vectice-image-puller.json” file. This is found in the package your Vectice account team provided you. Contact [email protected] if you require assistance. Use this file to create the secret that will be used to pull the docker images from the Vectice GAR registry.
Step 5: Install the Vectice Stack
From the package your account team provided, untar helm vectice chart and create myvalues.yml from values.yml file. Below, sample values are provided between brackets.
Please refer to the configuration page and comments inside the file myvalues.yaml to customize values.
Next, fill in the values in myvalues.yaml according to your environment deployment, and deploy Vectice global objects using Helm
Once this is done, retrieve the Vectice ingress IP. Note: this might take up to 5 minutes to appear
The expected output should look like this. Below are example values:
Finally, add the A record as a new entry in your DNS resolver.
Learn more about A DNS records.
In this example, the A record would look like below: